This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our seventh Threat Horizons Report (full version) that we just released (the official blog for #1 report, my unofficial blogs for #2, #3, #4, #5, #6, #7 and #8).
My favorite quotes from the report follow below:
- “Credential abuse resulting in cryptomining remains a persistent issue, with threat actors continuing to exploit weak or nonexistent passwords to gain unauthorized access to cloud instances, while some threat actors are shifting to broader threat objectives.” [A.C. — the new insight here is lack of change!]
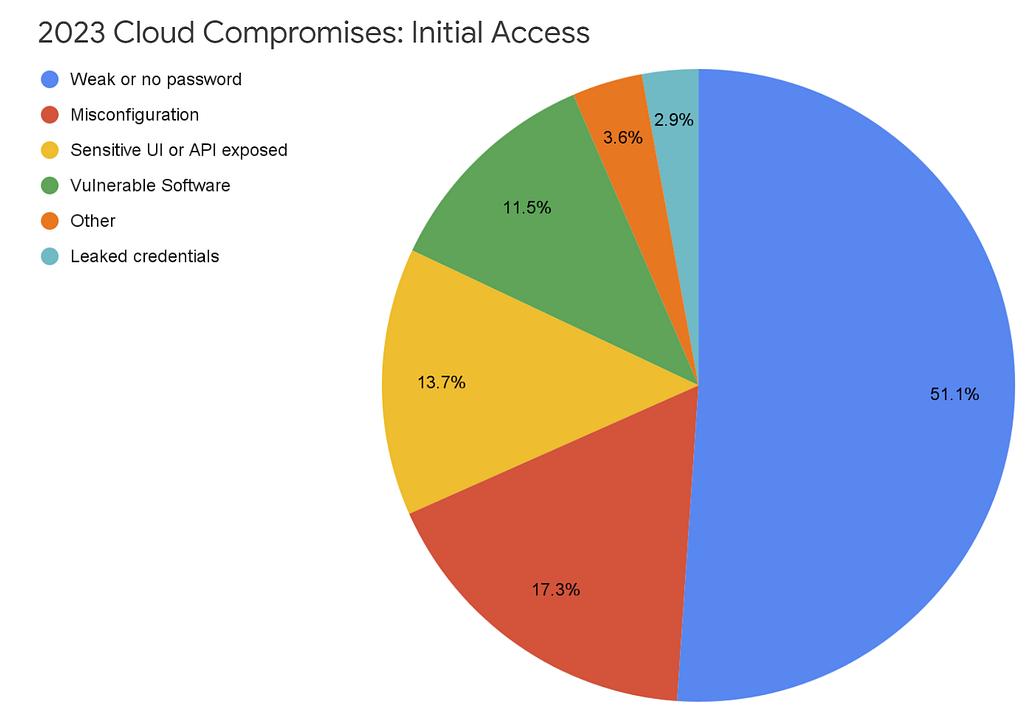
- “Credential issues remain the pr
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.This article has been indexed from Security BoulevardRead the original article: