Read the original article: Malvertising: Made in China

Two loosely related cybercrime groups operating scores of fake ad agencies from China are so deeply embedded in the ad tech industry that they can launch attacks that surpass the scale of the largest advertisers. At a time when China is under intense international scrutiny, these groups largely fly under the radar, raking in millions of victims in Europe and the US without drawing attention to their source.
In this article, we present eGobbler and their doppelganger Nephos7, their origins and what made them successful over time.
Setting the stage — Rise to success, 2017–2018

eGobbler rose to success by being one of the first groups to leverage javascript fingerprinting to target iOS. iOS being the least fragmented mobile environment, they understood that they could build very precise fingerprints for it, that would allow them to evade simulated environments as found in the security scanners of that time. Starting with JavaScript Sensor APIs and quickly moving to WebGL based fingerprinting, they essentially defeated user agent spoofing and gained unfettered Javascript execution on millions of end-users’ devices since then.
Stable scheme, with some twists
Since 2018, eGobbler has settled on a relatively sophisticated but slow evolving stack:
- Leverage ad platforms’ hosting to embed malicious code in HTML5 ad code. This is typically achieve by injecting the code in CreateJS or Greensock dependencies — libraries commonly found in HTML5 ads.
- Use of WebGL-based fingerprinting (among other tricks) to activate on victims’ devices only
- Geo-fencing, using basic server-side cloaking
- Use of commercial CDNs as reverse proxies (namely Rackspace and Fastly)
- Programmatic ad chains are typically made of an SSP call, a DSP call and optionally an adserver call. eGobbler is adept at creating artifical chains of ad tag redirections between multiple DSPs, which would never exist in the wild. The goal is likely to confuse analysts on the actual source of the ad.
- Through 2019, eGobbler slowly migrated to weekend activity. By 2020, they ended up exclusively running on weekends (and holidays) to maximize impact during off hours.
Considering eGobbler’s massive scale, this change of tactic alone is the main driver for the rise in general malvertising weekend activity since 2019
Breaking the browsers
Top malvertising groups see increased browser security around forced redirects as a threat and invest in finding flaws. To boost the efficacy of their payloads, eGobbler came up with a number of zero day exploits.
Detected by Confiant in 2019, CVE-2019–8771 and CVE-2019–5840 are browser vulnerabilities (Safari and Chrome) introduced by eGobbler and allowing them to bypass popup blocking and iframe sandboxing, which are protections against forced redirects (more here and here).
Enter Nephos7
Nephos7 started out in Q4 of 2019 with familiar tactics and techniques:
- Use of commercial ad servers to hide malicious code
- Use of commercial CDNs as reverse proxies (Cloudfront)
- Mimick instantiation of popular JavaScript APIs (e.g. Hotjar, Snowplow, etc.) to hide in plain sight
- Use of WebGL-based fingerprinting (among other tricks) to activate on victims’ devices only
- By end-of-year 2019, Nephos7 had aligned with eGobbler’s weekend patterns with a large attack on December 29.
Timeline of tactics and payloads
From Gift Card Scam to Carrier-branded Scams to Drive-by downloads, Nephos7 tightly follows eGobbler’s path across all dimensions.
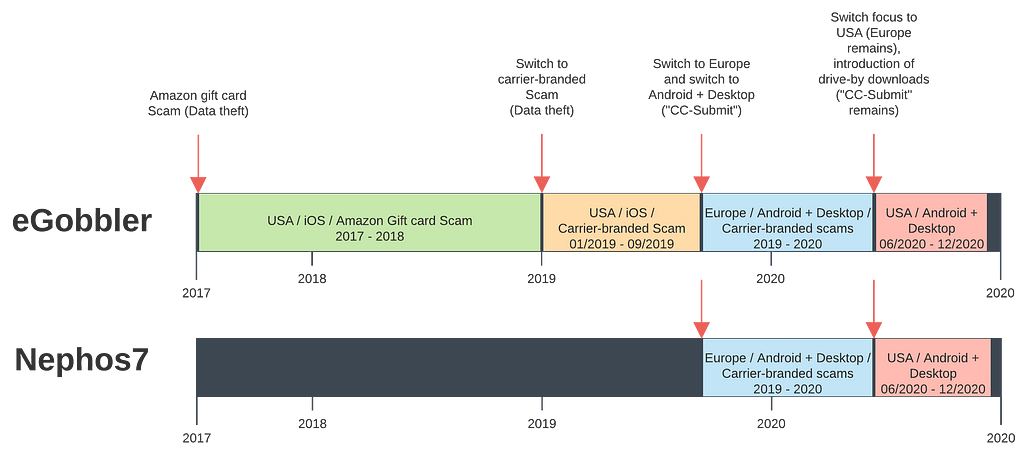
Not only the types of payloads align very closely but the landing pages bear a striking resemblance. As an illustration, below is a comparison of carrier-branded “CC-Submit” scams where the victim is presented with a fake message from their ISP (or mobile phone carrier) inviting them to enter their credit card information to confirm their prize.


From June 2020, both attackers switched focus to the United States and introduced drive-by download payloads. Below is a comparison of landing pages pushed by each threat actor in the US: Almost the same, dropping the same adware (different hashes), no overlap in infrastructure. Nephos7 wins with its “Premier Software Updater” ™.

Introducing “Holcus Installer”, the adware dropped by Nephos7 and eGobbler, research by Taha Karim– Lead Security Researcher, Confiant
eGobbler July25 campaign downloads a .msi file with the following sha-256 hash c818fe4c3fd3b0dbcfc3f17440e110c5a6ce3729382ffc88db8f83f830a115f9
Nephos7 July 26 campaign downloads a .msi file with the following sha-256 hash fb7d3f3914bf1722b3b369b23509b3746a44496bd3c78de91f27f8ee8d0ebead
Both of these .msi files unpack and run the same variant of a signed installer we dubbed Holcus Installer. The Holcus Installer samples we collected so far were all signed, and some of their features include:
- C2 communications via https, with certificate pinning checks. For example checks are performed on the certificate issuer string if it contains a substring CloudFlare, Cloudflare, or Let’s Encrypt before a communication is established.
- All Holcus Installer strings hinting to main functionality, C2 server, and executed commands are all encrypted with a custom RC4-like algorithm using key 2KNl6BKD94L2LyAY
- Holcus Installer checks if PUA detection (PuaProtection field) is enabled in the current Windows Defender configuration. This is done by via the wmi query: SELECT * FROM MSFT_MpPreference
- One variant of Holcus Installer we found, additionally checks the DeviceID of the keyboard retreived via wmi query: SELECT * FROM Win32_Keyboard
- Holcus Installer has the capability to download and execute binaries from the C2 server and sends hardcoded status messages to the C2 server by encoding them using a bin2hex encoding.
- Holcus Installer variants we collected have been observed communicating with the following C&C servers: myappcube[.]com, businessfulcrumsoft[.]com and softwaredatariver[.]com
- Holcus Installer uses a hardcoded User-Agent “NSIS_Inetc (Mozilla)” for C2 communications
- In our test environment, Holcus Installer was seen downloading and installing a decoy copy of notepad++ (sha256 hash bda85bc0bb7beb11dbb9e9a964a2e2f0e4d35d0fc1e6b769e32b6847bfed8296)
Explaining the striking resemblance
We think that the two groups are solely focused on redirecting visitors to malicious “offers” that are operated by different groups, themselves specialized in operating these schemes. Malvertisers can shop around with different affiliate marketers to get the best yield for their traffic. Somehow Nephos7 and eGobbler are shopping around at the same stores.
2020’s Largest Digital Marketers
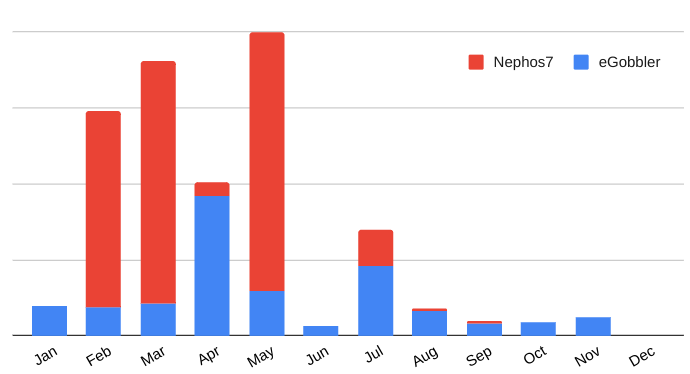
Both actors maintained presence through 2020, with Nephos7 being wildly successful in the first half of the year in Europe, while eGobbler maintained a steady pace and more successfully transitioned to targeting the US in the second half of the year.

In 2020, both actors achieved “web scale” on multiple occasions. No other malvertising group was (ever?) able to create anything comparable to this massive ecosystem disruption. Here are two examples:

Clocking at 5% of all display advertising on May 24th, Nephos7 arguably became (for an instant) the largest digital marketer in Europe. In comparison, eGobbler’s most significant spike “only” hit 2.3% on July 25th.
In total, in 2020, Confiant blocked 112 million ads from eGobbler and 198 million ads from Nephos7 on behalf of our online publisher clients. Extrapolating our data, we estimate 6 billion malicious ads were served by the two actors during the period.
Targeting
Device/OS targeting has been markedly different between the two actors. In 2020, eGobbler was heavily focused on targeting desktop computers (76%) while Nephos7 was more evenly split between mobile devices (52%) and desktop (48%).
As presented earlier, Nephos7 specifically targets Windows, excluding Mac OS X from its targeting.
Notably, in 2020 iOS only received a small fraction of hits from eGobbler (1.8%) while being completely excluded by Nephos7. Both actors have favored Android as their mobile platform of choice. This is all the more striking as eGobbler started out back in 2017 with a strong iOS focus.
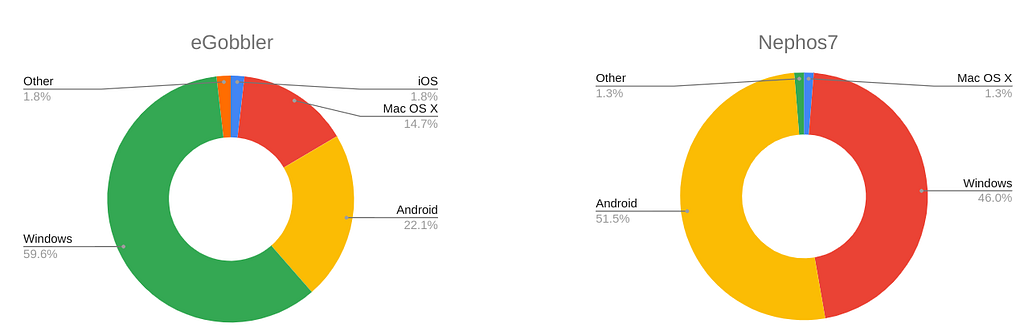
To achieve the sort of persistent scale that both actors enjoyed in 2020, they became experts at building relationships with “DSP” ad platforms. To enter the ad tech ecosystem, they worked to look reputable from all perspectives. That includes:
- Building a reputable looking corporate identity, with a legal entity registered far from “home” – more on this below.
- Using a commercial ad server to host ad creatives and give a semblance of buyer sophistication. In reality, well-tuned commercial ad servers can achieve incredibly powerful cloaking for malvertisers.
- Running dummy ad campaigns for weeks or months at low volumes (to build reputation) before flipping the switch.
Hunting Corporations
Programmatic advertising has been architectured such that online publishers have little oversight or visibility on campaigns that are running on their sites. What will start running at full throttle at 8 am on a quiet Sunday morning (eGobbler’s and Nephos7’s favorite modus operandi) is left to sheer unpredictability.
The situation is quite different if you take the perspective of a DSP. To qualify for the kind of scale that these threat actors are craving for, customers typically go through a thorough approval process, mostly focused on assessing risk based on reputation.
Burn and Repeat
Once they’ve committed their deed, the abused DSP forever bans the offending entity used to finance the malicious ad campaign. This constraint shapes for our attackers a fairly simple game plan:
- Create many legal entities,
- Burn them one by one with each DSP
- Repeat.
Due to the lack of industry-wide buyer transparency, malicious entities have the leisure to strike repeatedly without fear of industry-wide ban. We at Confiant sponsor an initiative to provide this transparency: buyers.json.
Network of Organized Crime
Over time, Confiant’s security team started to methodically pin attacks to their corresponding legal entities. This effort could not have been possible without the cooperation of many impacted DSPs (thank you!).
Nephos7 Entities

We believe Wooden Ads started operating some time in Q4 of 2019 as the first Nephos7 front company making the rounds through the major DSPs. With an incorporation in November 2017, one can only wonder what this company was previously used for. The level of sophistication we’ve identified right from its inception is consistent with a previous life in malvertising.
Despite a remarkable streak of Wooden Ads activity, it soon became time to invoke more legal entities to establish more DSP connections. By June, Nephos7 started rolling out a wide range of entities that had been patiently staged since 2018. Incorporated in Colorado in March and October 2018 respectively, AdSige and SignalAds both appeared on our radar in June 2020 in separate attacks. In total, between June and November, 8 entities were responsible for Nephos7 attacks. Paradoxically, this is also a time of decreased success, characterized by an inability to generate any significant volumes after July.





While looking up the directors of Nephos7 entities (all individuals residing in China), we identified many more dormant companies based in the UK, also established in 2018 and in good standing as of late 2020, likely r
[…]
Read the original article: Malvertising: Made in China