Microsoft Breach — What Happened? What Should Azure Admins Do?
On January 25, 2024, Microsoft published a blog post that detailed their recent breach at the hands of “Midnight Blizzard”. In this blog post, I will explain the attack path “Midnight Blizzard” used and what Azure admins and defenders should do to protect themselves from similar attacks.
The Attack Path
Step 0: The adversary used password guessing to gain initial access into a “test” tenant.
Step 1: The adversary used this access to “compromise” an app registration in the test tenant (Figure 1).

I interpret the word “compromise” here to mean the adversary added a new credential to the app registration object. We don’t know from Microsoft’s blog post how exactly this user was able to do this. These are the Entra ID roles that allow a user to add new credentials to any app within the tenant:
- Application Administrator
- Cloud Application Administrator
- Directory Synchronization Accounts
- Global Administrator
- Hybrid Identity Administrator
There may have also been a custom role, or the user was possibly added as an owner of the app registration. Conversely, the user may have potentially had one of the following roles, which allow escalation to any role including Global Administrator:
- Partner Tier2 Support
- Privileged Role Administrator
Step 2: The adversary rode existing configurations to gain “elevated access” into the Microsoft corporate Entra ID tenant (Figure 2).
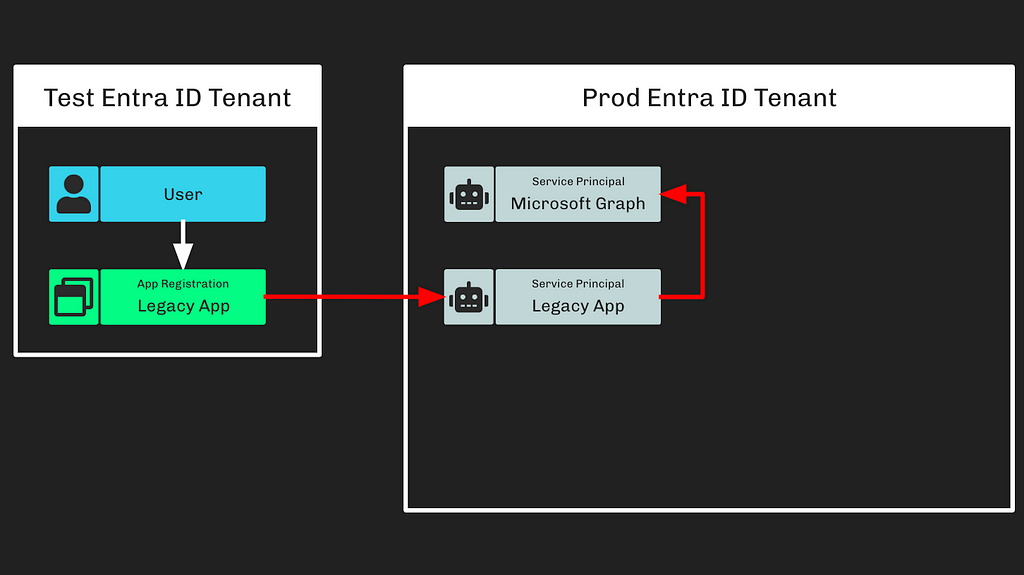
This means that the “legacy” app registration from the test tenant was instantiated as a service principal in the corporate tenant. The privileged actions taken later on led me to believe that this “Legacy App” service principal either had one of the following Entra ID roles:
- Global Administrator
- Partner Tier2 Support
- Privileged Role Administrator
Or one of the fo
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: