Read the original article: Microsoft Exchange: Patching Too Late If Already Compromised
On March 2, 2021, Microsoft accused a Chinese APT group which they name Hafnium of compromising 30,000 Exchange servers. They announced four security vulnerabilities, known as 0-days, which refers to the fact that attackers had a reliable means of exploiting the vulnerability for which there was no patch. In case your organization didn’t go into full panic mode, GO PULL THE FIRE ALARM! THIS IS SERIOUS!
Tom Burt, Microsoft’s VP of Customer Security & Trust, released a blog post about Hafnium: New Nation-State Cyberattacks. Microsoft describes Hafnium as “primarily targeting entities in the United States for the purpose of exfiltrating information from a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks and NGOs.” According to my favorite APT Cross-reference chart, maintained by Florian Roth (Twitter: @Cyb3rOps) Hafnium is also referred to by Symantec as Ant. (They chose the name because one of the common webshells used for post exploitation was regularly hit by a web browser using the user agent “antSword/v2.1”. Both AntSword (中国蚁剑 ) and ChinaChopper (中国菜刀) are popular webshells used by Chinese attackers for many years.
FireEye says there is no reason to believe the activity is limited to one threat actor and refers to the clusters of attacks as UNC2639, UNC2640, UNC2643.
FireEye associates UNC2639 with activity from IP addresses 165.232.154.116 and 182.18.152.105, both active at the time of the Microsoft announcement (March 2 and March 3).
FireEye associates UNC2640 with activity involving “web shell” files named “help.aspx” (MD5 4b3039cf227c611c45d2242d1228a121) and “iisstart.aspx” (MD5 0fd9bffa49c76ee12e51e3b8ae0609ac)
FireEye associates UNC2643 with the deployment of a Cobalt Strike Beacon (MD5 79eb217578bed4c250803bd573b10151) and the IP addresses 89.34.111.11 and 86.105.18.116.
FireEye says they began seeing this activity in January, which matches the reports from Microsoft that they were notified of this activity by security firm Volexity in January, however DEVCORE Research Team gets credit for trying to exploit marketing of the bug by calling the attack “ProxyLogon” and making a sexy webpage and logo for the attack, a la HeartBleed. Fortunately, that really hasn’t caught on, however their timeline is still very interesting. They found the first bug 10DEC2020 and the second 30DEC2020 and reported both to Microsoft on 05JAN2021 (as Tweeted by their Taiwanese researcher, Orange Tsai.)
Symantec makes clear that the actor which they call Ant (and Microsoft calls Hafnium) is definitely no longer the only attacker using these vulnerabilities. Symantec’s diagram of the attack is useful:
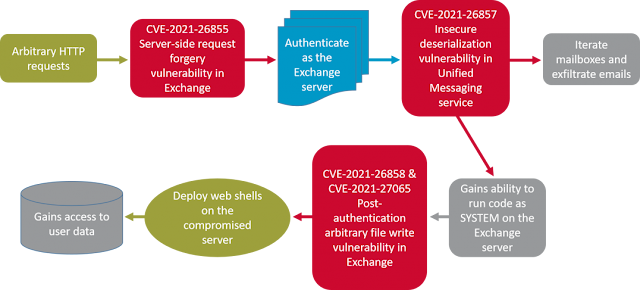 |
| Symantec’s attack flow diagram |
Brian Krebs interviewed several researchers about the attack, including Steven Adair, who says his company, Volexity, has been seeing the bug since 06JAN2021. See Krebs on Security: “At Least 30,000 US Organizations Newly Hacked via Holes in Microsoft’s Email Software.”
As Krebs and others have since pointed out, while 30,000 US-based organizations were known to be victims of Hafnium/Ant, now that the vulnerability is known, the attacks have grown to an astronomical number. Why is this a problem? The companies most likely to be running their own unpatched mail servers are also the least likely to be clueful enough to patch.
Both Forbes and WIRED now say that hundreds of thousands of servers have been compromised and the compromise count at one point was growing by “thousands per hour.”
What To Do? PATCH! (But it is quite possibly too late…)
Obviously, the most important thing to do is apply Microsoft’s patches. However it is VERY IMPORTANT TO UNDERSTAND that you may already be compromised. Patching DOES NOT make you “un-hacked!” Patch, but also follow the guidance from CISA on determining if you are already hacked.
The vulnerabilities are listed here, each linking to the Microsoft security alert associated with the CVE.
WHAT TO DO? SEE IF YOU ARE HACKED!
The CyberSecurity & Infrastructure Security Agency, CISA, part of the Department of Homeland Security, has provided comprehensive information on how to detect the attack, including a nice guide on how to use FTK Imager to capture memory from your Exchange Server and where to look for evidence of being compromised.
Please thoroughly review their recommendations found as Alert AA21-062A.
Many of their indicators come from Volexity, who also shares a video explaining the attack in their blog post from 02MAR2021, “Operation Exchange Marauder.” It should be noted that neither of the IP addresses from FireEye are included on this list.
In addition to the CISA guidance, Microsoft has released a script which can be run on your Exchange Server to look for signs of being compromised. Their script is described in their Hafnium Targeting Exchange Servers blog post, but a direct link to the script is:
https://github.com/microsoft/CSS-Exchange/tree/main/Security
This script scans the HttpProxy logs, the Exchange logs, and the Windows Application event logs for signs of exploitation. Hopefully the bad guys haven’t WIPED the logs!
Read the original article: Microsoft Exchange: Patching Too Late If Already Compromised
